Public keys Vs. private keys
IN BRIEF: Symmetric and asymmetric cryptography. The problem of key distribution. What are private keys? Why should we keep the private key safe?

🇧🇷 Portuguese version: here.
What are cryptographic keys?
A cryptographic key is a string of data used to encrypt data (to keep the data secret), decrypt data (to perform the reverse operation), sign data (to ensure that the data is authentic) or to verify a signature.
Encryption keys come in two forms: symmetric or asymmetric.
Forms of encryption
In a symmetric algorithm, the key for encrypting and decrypting is the same.
In an asymmetric algorithm, the keys are different, with the encryption key being called the public key and the decryption key being called the private key.
Symmetric encryption Vs. Asymmetric encryption
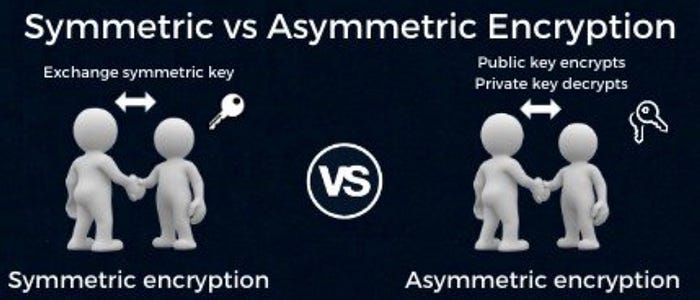
- Symmetric encryption uses a single key that needs to be shared between the people who need to receive the message, while asymmetric encryption uses a pair of public keys and a private key to encrypt and decrypt messages during communication.
- Symmetric encryption is an old technique, while asymmetric encryption is relatively new.
- Asymmetric cryptography was introduced in the 1970s to complement the problem inherent in the need to share the key in the symmetric cryptography model, eliminating the need to share the key by using a pair of public and private keys.
- Asymmetric cryptography takes relatively longer than symmetric cryptography.
Using an asymmetric algorithm for data authentication
We usually think of an asymmetric signature and verification algorithm to authenticate data. There’s nothing better than an example to understand something…
Imagine that Ana wants to send a secret message to Beto. Using symmetric cryptography, Ana will generate a cipher [X] — or key — to encrypt this data, before sending it to Beto.
When Beto receives the encrypted message, he can decrypt it using the X key. This is when a problem arises…
The key distribution problem
How does Beto get access to the key [X] to decrypt the message, without compromising security?
Of course, the key [X] cannot be sent openly. That’s why Beto needs a different technique to gain access to this secret key [X]. This is known as the key distribution problem.
This problem was solved in the 1970s with the invention of the asymmetric form of cryptography — already mentioned — which is generally referred to as public key cryptography.
Public key cryptography or asymmetric cryptography
Public key cryptography, also known as asymmetric encryption, is any cryptographic system that uses key pairs. Public keys are those that can be widely disseminated, and private keys are known only to their owners.

Using public key cryptography, in the case of Ana and Beto, Ana sends her message to Beto and encrypts it using his public key. Anyone can intercept the message, but only Beto can decrypt it using his private key.
This key pair performs two functions: authentication and encryption.
In authentication, the public key verifies that the holder of the paired private key can decrypt the message encrypted with the public key;
In encryption, only the holder of the paired private key can decrypt the message encrypted with the public key.
The two users [Ana and Beto] only exchange their keys to access and review this information, and the party can revoke this access at any time.
So what is a private key?
Private key: what do you need to know?
A private key, also known as a secret key, is a variable in cryptography used with an algorithm to encrypt and decrypt data.
Secret keys [private keys] should only be shared with the generator of the key or the parties authorized to decrypt the data.
Private keys play an important role in symmetric cryptography, asymmetric cryptography and cryptocurrencies.
A private key is usually a long sequence of bits, generated randomly or pseudo-randomly, which cannot be easily guessed. The complexity and length of the private key determine how easily an attacker can carry out a brute force attack, in which they try out different keys until they find the right one.
Benefits associated with the use of private keys
- Security. Longer private keys with greater entropy, or randomness, are more secure against brute force or dictionary attacks.
- Speed. Symmetric key cryptography is faster from a computational point of view than asymmetric cryptography with its public-private key pairs.
- Better for encryption. Most cryptographic processes use private keys to encrypt data transmissions.
- It works for stream and block ciphers. Private key ciphers [the algorithm for encrypting and decrypting data] generally fall into one of two categories: stream ciphers or block ciphers. A block cipher applies a private key and an algorithm to a block of data simultaneously, while a stream cipher applies the key and algorithm one bit at a time.
Public key management challenges
The security of encryption keys depends on choosing a strong encryption algorithm and maintaining high levels of operational security. Cryptographic key management is necessary for any organization that uses cryptography to protect its data — be it symmetric or asymmetric cryptography.
Although private key cryptography can guarantee a high level of security, the following key management challenges must be considered:
- Management. Diligent management of private keys is necessary to protect them from loss, corruption or unauthorized access.
- Continuous updating. Private keys used to encrypt sensitive data must be changed regularly to minimize exposure in the event of leakage, loss, corruption or unauthorized access.
- Recovery and loss. If an encryption key becomes inaccessible, the data encrypted with that key will be unrecoverable and lost. This is why Ledger recently launched its Recover program — see the analysis of the risks and possible impacts of Ledger Recover here.
Private keys vs. public keys
As we saw earlier, asymmetric cryptography — also known as public key cryptography — uses pairs of public and private keys. These two different but mathematically linked keys are used to transform plain text into encrypted cipher text or encrypted text back into plain text.
When the public key is used to encrypt the ciphertext, that text can only be decrypted using the private key. This approach allows anyone with access to the public key to encrypt a message, and only the holder of the private key can decrypt it.
When the private key is used to encrypt the ciphertext, this text can be decrypted using the public key. This ciphertext can be a component of a digital signature and be used to authenticate the signature. Only the holder of the private key can have encrypted the ciphertext, so if the related public key manages to decrypt it, the digital signature will be verified.
The public key is made available to everyone who needs it in a publicly accessible repository. The private key is confidential and should only be accessed by the owner of the public key pair. In this method, anything encrypted with the public key requires the related private key for decryption, and vice versa. Public key cryptography is usually used to protect communication channels such as e-mail.
Application of public keys and private keys in cryptocurrencies
In cryptocurrency, public keys are assigned to wallets, and a public key is valid if there is any cryptocurrency in the wallet.
Taking the example from the beginning of this article, in order for Ana to send bitcoin (BTC) to Beto, she simply signs a transaction with the private key associated with the wallet from which she is spending the money [A] .
The transaction says that the bitcoin [BTC] associated with Ana’s wallet [A] should be assigned to the wallet with Beto’s public key [B]. The miners validating the transaction need to check that Ana’s [A] wallet has enough bitcoin and that the signature is correct. They don’t need to know who Ana or Beto actually are.
Final thoughts
As the use of the public Internet continues to expand for commercial, governmental and personal communications, so does the need to use encryption securely to protect transactions and businesses.
For this reason, it is very important to maintain the privacy of private keys which, used to protect confidential data, become the basis for maintaining security in all types of communication.
